The invention and application of smart card technology is a major revolution in computer technology. It is widely used as a personal identification and security information carrier in many fields such as finance, medical treatment, transportation, telecommunications, and so on, affecting in depth the production of budding people. life. The asset value of a single smart card to protect may not be high, but the amount of assets involved in the entire smart card field may be huge; the attacker's profit from breaking a single card may not be comparable to his efforts, but the experience gained after successful breakthrough It may make it easier to attack similar cards, and subsequent cumulative profits will be enormous. Therefore, the hardware attack technology for smart cards has been continuously developed in recent years, and at the same time, compared to other expensive information technology products, smart cards are inexpensive, usually between tens and hundreds of yuan, so the attacker only needs to spend a lot of money. At a small price, multiple smart cards can be obtained for aggressive testing. Therefore, the security threat faced by the smart card is more and more severe. However, the hardware security hardening implemented to protect the smart card is relatively expensive. Finding a low-cost and effective smart card security protection technology is particularly important.
2 Smart Card Common Hardware Attack Methods
There are many hardware attack methods for smart cards. According to the attack behavior, the intrusion smart card hardware can be divided into two categories: active attack and passive attack.
2.1 active attacks
The common active attack behaviors for smart cards are hardware decomposition, electromagnetic interference, and perpetual variation. Their common feature is the use of certain tools such as etching tools, optical microscopes, probe stations, laser cutting machines, scanning electron microscopes, and focusing. Ion beams, etc., will cause varying degrees of damage to the integrity of the smart card. Some other easy-to-follow attack techniques are introduced. According to the timing of the attack, active attacks can be divided into two categories. One is to obtain the data and code inside the card body in a static condition. One is to break through or bypass the security mechanism of the smart card to obtain sensitive information under dynamic operation.
2.2 Passive attacks
Unlike active attacks, using passive attacks to capture smart card information is less straightforward and accurate, but its impact on smart cards is reversible. Moreover, the types of passive attacks are not limited to one aspect of hardware attacks. However, it is widely present in attacks on communications, interfaces, COS, and other aspects.
2.2.1 Information Leakage Model
The most basic passive attack method is the observation method. The observation method is based on the information leakage model of the program or cipher algorithm in the execution process, as shown in Figure 1.
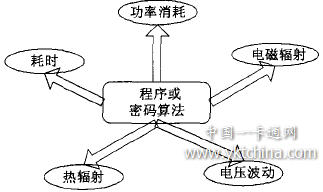
Figure 1 Information leakage model
Observed objects can be the consumption of electrical energy for a certain period of time, the fluctuation of voltage, and also the information of changes in the intensity of electromagnetic radiation, and then analyze their function with time to find out the laws. According to different observation objects and angles, they can be roughly divided into the following types of attacks:
2.2.2 Power Analysis
In June 1998, Kocher et al. proposed a power analysis attack method, that is, a power value determined according to a known operation. Directly analyze the power data recorded when the cryptographic algorithm was run. Common simple power analysis (SPA) ~ 1 rate differential attack (DSA). By analyzing the power consumption signal, the Hamming weight information of the processor is being processed, and the information can be used to construct the equivalence relationship in the data, and thus the password can be deciphered.
2.2.3 Electromagnetic Radiation Analysis
As an electronic device, the components of a computer often generate electromagnetic radiation during operation. If an attacker can detect electromagnetic radiation and find their relationship with the underlying calculations and data, it is possible to obtain a considerable amount of information related to these calculations and data. Similar to power analysis, electromagnetic radiation attack fEMA1 can also be divided into two categories: Simple Electromagnetic Radiation Analysis (SEMA) ~ Divided Electromagnetic Radiation Analysis (DEMA).
2.2.4 Analysis of Time-consuming Information
Due to performance optimizations, branch and conditional statements, RAM buffer hit rates, or processor instruction execution times that are not fixed, there may be slight differences in the time spent by an encryption system for different inputs. The time-consuming information attack is based on the measurement of the operation time of the basic arithmetic unit of the encryption system. This may lead to leakage of key-related information. For example: by carefully measuring the time required to complete the operation of the private key. The attacker can find the same parameter in the Diffie-Hell-man key exchange protocol or the key factor in the RSA algorithm, then decipher the other cryptosystems, and give an example of the time-consuming information attack on the RC5 algorithm.
3 Software-based coping strategies
Against these hardware attack means. The usual protection measure is to use hardware protection measures such as adding a protective layer, installing a security sensor, chaotic wiring of the chip, memory bus encryption, and memory access control. However, hardware protection methods have the disadvantages of high cost and poor flexibility. The French scholar Xavier Leroy proposed a way to use software methods to guard against hardware attacks. And studied from the perspective of programming language and static analysis. We call this kind of thinking "software defense". According to this idea, this paper further proposes several specific strategies and methods for hardware attacks in smart card embedded software design.
3.1 The basic connotation of "software defense" thought
Xavier Leroy pointed out in his article: "The key to using software methods to deal with hardware attacks is to see that any hardware attack can not freely change the way the hardware itself operates." This is also the basic connotation of "software defense" thinking.
Take for example the various types of hardware attacks listed in Part 3: Although active attacks have the advantages of accuracy and efficiency, they can cause irreversible damage to the smart card hardware. This will be easily detected by the presence of security sensors in the smart card, of course, we can also use software methods to detect, such as running a periodic self-test program: passive attacks, although it will not cause irreversible impact on the hardware, but Its impact on specific sensitive information is inaccurate. For example, using focused ion beam illumination can instantaneously change the data stored on the card to all zeros or all ones. However, the data at a specific location on the memory is changed to 0 or 1.
3.2 Specific Methods of "Software Defense"
3.2.1 Data redundancy
In order to prevent the hardware attack from modifying the static data and program code on the smart card storage, a certain length of redundant data may be added when storing the data f and the program code 1 to ensure the integrity of the data. A simple method is to add a cyclic redundancy code after each set of data. If you have stricter requirements for data integrity, you can use a simple hash function to calculate the hash value for each set of data.
Through data redundancy, it is also possible to effectively prevent the active attack from modifying key data in the smart card (such as security bit, instruction download control bit, etc.), and because only changes to the data storage format, this measure can not affect the card. In the case of the original program structure inside, the security of the smart card is reinforced.
3.2.2 Controlling Redundancy
For the tampering of static data or key code, we can effectively defend against data redundancy. However, in the process of dynamic execution of the program, the data redundancy strategy is powerless, so it is also necessary to increase the redundancy that is controlled during program execution. The main idea of ​​controlling redundancy is to add multiple controls to functions that contain key code to ensure that program execution is in a completely secure and trustworthy environment. For example, multiple status bits are set, and the state of these status bits is constantly checked during execution of the program. If one of the status bits changes, the program immediately exits execution. 
3.2.3 Performing Redundancy
Unlike active attacks, smart card passive attacks exploit the card-in-a-box procedure (the information leakage model of cryptographic algorithm 1 during execution. It does not cause any irreversible damage to the smart card. Therefore, the passive attack on the smart card must also be based on the information leakage model of the smart card. Start.
For ease of understanding, we assume that there are two separate f logics in the card program f cryptographic algorithm 1 that do not logically have an inheritance relationship, and that there is no sequential relationship 1 code segments C1 and C2, and the code segments can be different levels, either Large to independent functional functions, can also be simple 0 and 1. It is not difficult to understand that it is due to the differences between C1 and C2 that eventually led to the generation of various kinds of information during program execution. In order to avoid leakage of information, the most fundamental method is to reduce the generation of such information as much as possible. The literature introduces ways to reduce information generation at the coding level. This paper presents a simple yet effective method to reduce information leakage at the level of program function function-execution redundancy.
For the two independent function functions C1 and C2 described above, we can design a random function generator Random0 when writing the program. Its output is an equal probability distribution of O and 1. At this point our code can be modified like this: 
of course. This is just a simple realization of this idea. If it is more than one function. We must appropriately modify our random number generator and conditional decision structure. If there is no such independent function in the program, then we also need to construct several different but equivalent implementations of the same function.
In short. The specific methods of software defense are aimed at the specific weak points of the hardware security of the smart card, and adopt the methods of data redundancy, control redundancy, or execution redundancy to implement targeted security reinforcement. Because it is a software method, compared with hardware security hardening, it only requires simple modification of the code, which is very cost-effective.
4 Conclusion
Although the above-mentioned software defense technology is relatively simple to implement, it often requires centralized planning during the entire system design process to control the program execution enough to effectively resist various hardware attack behaviors. Moreover, whether it is data redundancy, control redundancy or execution redundancy will add a certain degree of burden to the realization of system functions. The next step can be considered to reduce these costs by comprehensively using modern programming techniques.
The author of this thesis innovates: It concludes a smart card information leakage model: based on the idea of ​​"software defense", it proposes several low-overhead, high-efficiency software defense measures and methods that are resistant to hardware card security threats.
[1] Oliver K0mmerling and Markus Kuhn. Design Principles for Tamper-Resistant Smartcard Pmcessom. Chicago: Proceedings of USENIX Workshop on Smartcard Technology, 1999: 9-20.
[2]Thomas S. Messerges, Ezzy A. Dabbish, Robert H_Sloan. Eamining Smart-Card Security under the Threat of Power Analysi6 Attacks. IEEE Transactions on Computers, 2002, (51): 541-552.
[3] Paul Kocher, Joshua Jafe and Benjamin Jun. Introduction t!DDiferential Power Analysis an d Related Attacks. Http'. //. Com/dpa/technica1.
[4] Xavier keroy. Computer security from a programming languagean d static analysis perspective. Http://pauillac. Inria. Fr/~xlemy/publL
[5] Ross Anderson, Markus Kuhn. Low Cost Attacks on Taml~?Resistance Devices. Springer-Verlag: 5th International Workshop, LNCS, 1997 (1361): 125-136.
[6] Helena Handschuh, Howard M. Heys. A Timing Attack on RC5. Http://. Man. Ca/-howard/PAPERS. 2004
[7] Simon Moore, Ross Anderson, Robert Mullins. Balanced SeIf-Checking Asynchronous Logic for Smart Card Applications. Http://WWW. C1. Cam. Ac. Uk/-swml 1/research/papers. 2002
[8] Cao Ning, Feng Yi. Smart card security and application. Microcomputer information.
About the Author:
Chen Shichao (1982.10 a), male (Han), Shangqiu of Henan Province, graduated from the PLA Information Engineering University, is now mainly engaged in public key infrastructure, smart card system research;
Xu Kaiyong (1963.4 1), male (Han nationality), Luoshan, Henan Province, master's tutor and researcher of PLA Information Engineering University, is currently mainly engaged in military information security system design, public key infrastructure research;
Chen Guang (1978.6 a), male (Han), Henan Zhumadian, master, lecturer, is now mainly engaged in public key infrastructure, smart card system research;
Li Fulin (1980.2 a), male (Han), Chengde, Hebei, master, assistant teacher, is now mainly engaged in public key infrastructure, network information security research.
Mailing address: (450004 Institute of Electronic Technology, PLA Information Engineering University, No. l2, Shangcheng East Road, Zhengzhou, Henan Province) Chen Shichao
Classic Cast Iron Clawfoot Bathtub Design. Feet Available in White , Black, Polished Chrome, Brushed Nickel and Oil Rubbed Bronze.
A double-ended clawfoot tub offers convenient versatility in the bathroom. With two identical ends, one can recline at either end of the bathtub and achieve maximum comfort. Cast iron construction has proven to be a long-lasting substance that maintains its beauty year after year.
Different from drop in cast iron bathutb, Freestanding Cast Iron Bathtub can be installed in your bathroom more flexibly. Apart from skirted cast iron bath tub, we also suppy clawfoot cast iron tubs and pedestal porcelain enamel bathtubs.
When cleaning a cast iron bathtub always use a soft damp cloth or sponge with a non abrasive cleaning product. Stubborn marks can be removed using non-abrasive cleaning agents, such as washing up liquid, It is recommended that you rinse after each use of cast iron bathtub and also after cleaning. For a more extensive cleaning, clean with a gentle soap, such as a dish washing liquid or an all-propose cleaner.
Porcelain enamel of a freestanding bathtub or drop in bathtub can be chipped if it sustains a very hard impact. If this occurs, we recommend the services of a professional to repair the damaged area.
WHO WE ARE
Established in 1996, Anping Sunshine Sanitary Ware covers an area of 50,000 square-meters. We`re manufacturer in the field of bathroom and kitchen cast iron products, such as cast iron bathtub, Cast Iron Sink, and shower tray, with strong production capacity and production lines of gravity casting and vacuum casting.
We`ve past certifications of CE, cUPC and ISO 9001:2015 to ensure customers rest on the quality. We have professional designers to provide customized services and own a professional QC system to control the production process from the very beginning to the end. Our sales team are dedicated to customers` all needs and provide continued support.



Clawfoot Bathtub,Cast Iron Clawfoot Tub, Double Slipper Bathtubs
Anping Sunshine Sanitary Ware Co., Ltd. , https://www.sunshinebathtubs.com